[Solved] Critical UEFI Secure Boot Vulnerability (CVE-2024-7344)

Introduction
In January 2025, cybersecurity researchers uncovered a severe vulnerability in the Unified Extensible Firmware Interface (UEFI) Secure Boot system, tracked as CVE-2024-7344. This vulnerability poses a significant threat as it allows attackers to bypass Secure Boot protections, enabling the execution of unauthorized code during the boot process. Exploiting this flaw can lead to the deployment of persistent bootkits, which compromise system integrity and evade traditional security measures.
This blog will delve into the details of UEFI Secure Boot, the nature of the CVE-2024-7344 vulnerability, its risks, and the steps required to mitigate its impact.
What is UEFI Secure Boot?
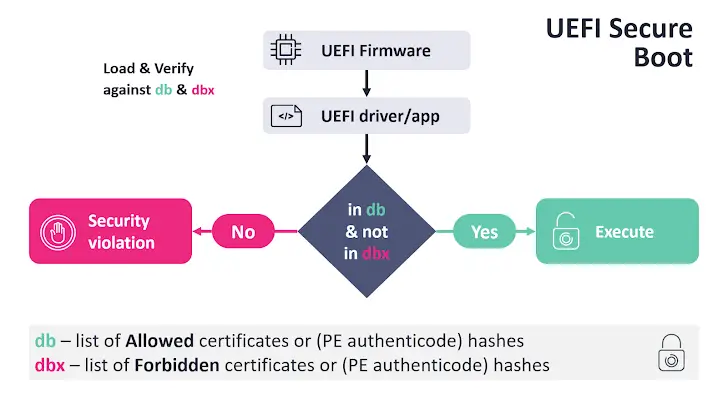
UEFI Secure Boot is a fundamental security feature within the UEFI specification. It ensures that the system boots using only trusted software authenticated by the hardware manufacturer. The mechanism involves:
- Digital Signature Verification: Secure Boot verifies the digital signatures of bootloaders, kernel images, and other critical components.
- Prevention of Unauthorized Software: Only software trusted by the manufacturer is permitted to execute during the boot process.
By validating the integrity of the boot process, Secure Boot acts as a first line of defense against boot-level malware.
CVE-2024-7344 Vulnerability Explained
The CVE-2024-7344 vulnerability arises from the improper implementation of custom Portable Executable (PE) loaders in certain UEFI applications. Instead of using standard UEFI functions such as LoadImage and StartImage, these custom loaders bypass critical security checks, allowing the loading of any UEFI binary—including unsigned and malicious ones—from a specially crafted file named cloak.dat.
Key Characteristics:
Custom Loader Flaw: These loaders fail to enforce the robust security checks integral to Secure Boot.
Bypassing Protections: This flaw enables the execution of untrusted code during the system’s startup phase.
Persistent Threats: Attackers can install bootkits that embed deeply into firmware, eluding detection and making them challenging to remove.
Affected Devices and Software
The following products are confirmed to be vulnerable if not updated:
- Howyar SysReturn (versions before 10.2.023_20240919)
- Greenware GreenGuard (versions before 10.2.023-20240927)
- Radix SmartRecovery (versions before 11.2.023-20240927)
- Sanfong EZ-back System (versions before 10.3.024-20241127)
- WASAY eRecoveryRX (versions before 8.4.022-20241127)
- CES NeoImpact (versions before 10.1.024-20241127)
- SignalComputer HDD King (versions before 10.3.021-20241127)
Users and organizations relying on these tools should prioritize updating to patched versions to mitigate the risk.
Risks and Exploitation
Exploiting CVE-2024-7344 allows attackers to:
Maintain Stealth: Persistent bootkits enable attackers to operate undetected for extended periods.
Exfiltrate Sensitive Data: Intercept credentials, encryption keys, and other critical information.
Compromise Networks: Use the compromised system as a foothold to target other devices within an organization.
Persistent Bootkits:
These malicious components operate at the firmware level, loading before the operating system. Their deep integration into the system makes detection and removal exceedingly difficult, especially for conventional antivirus and endpoint detection solutions.
Detection and Applicability Check
PowerShell Commands for Windows:
To determine if your system is affected, use the following PowerShell commands (run with elevated permissions):
Check Vulnerability:
[System.Text.Encoding]::ASCII.GetString((Get-SecureBootUEFI db).bytes) -match ‘Microsoft Corporation UEFI CA 2011’
Returns True if your system is affected.
Check Protection on 64-bit UEFI Systems:
[BitConverter]::ToString((Get-SecureBootUEFI dbx).bytes) -replace ‘-‘ -match ‘cdb7c90d3ab8833d5324f5d8516d41fa990b9ca721fe643fffaef9057d9f9e48’
Check Protection on 32-bit UEFI Systems:
[BitConverter]::ToString((Get-SecureBootUEFI dbx).bytes) -replace ‘-‘ -match ‘e9e4b5a51f6a5575b9f5bfab1852b0cb2795c66ff4b28135097cba671a5491b9’
Linux Systems:
For Linux users, updates are distributed through the Linux Vendor Firmware Service. Use the following commands to verify revocations:
Check for Revocations:
dbxtool –list | grep ‘cdb7c90d3ab8833d5324f5d8516d41fa990b9ca721fe643fffaef9057d9f9e48’
Check for Alternative Revocations:
dbxtool –list | grep ‘e9e4b5a51f6a5575b9f5bfab1852b0cb2795c66ff4b28135097cba671a5491b9’
Mitigation Strategies
1. Apply Patches
Vendors have released updates for their affected products. Users must upgrade to the latest versions immediately:
- Howyar SysReturn (10.2.023_20240919 or later)
- Greenware GreenGuard (10.2.023-20240927 or later)
- Others as specified.
2. Update Secure Boot Revocation Lists
Microsoft included revocations for affected UEFI binaries in their Patch Tuesday updates on 14 January 2025. Ensure your system’s revocation lists are up to date.
3. Monitor System Integrity
Leverage tools capable of detecting unauthorized firmware changes. UEFI integrity monitoring solutions can alert users to malicious modifications.
4. Enable Firmware-Level Security Features
Where available, enable hardware-based protections such as:
Intel Boot Guard
AMD Platform Secure Boot
Additional Measures
Managed Access to EFI Partition
In most UEFI bootkit scenarios, attackers modify the contents of the EFI system partition. Restrict access to this partition to prevent unauthorized modifications.
UEFI Secure Boot Customization
Customizing Secure Boot settings, as recommended by the NSA’s UEFI Secure Boot Customization report, can reduce the attack surface and facilitate quicker revocation updates.
Remote Attestation with TPM
Trusted Platform Module (TPM) remote attestation validates UEFI boot components against known-good configurations, detecting unauthorized modifications.
Lessons and Best Practices
The discovery of CVE-2024-7344 underscores critical lessons for maintaining firmware security:
- Avoid Custom PE Loaders: Developers should adhere to standard UEFI functions for binary loading and verification.
- Regular Firmware Updates: Organizations should prioritize timely updates, adhering to best practices like Cyber Essentials, which mandates installing all High and Critical rated patches within 14 days of release.
- Adopt Zero Trust Principles: Assume all components are potentially vulnerable, continuously verifying their integrity.
- Educate IT Teams: Train IT staff to recognize and respond to firmware-level threats effectively.
Conduct Regular Penetration Testing: Periodic testing helps identify vulnerabilities and Indicators of Compromise (IoC).
Closing Summary
As attackers increasingly target low-level systems to evade traditional defenses, organizations must proactively secure their infrastructure. By applying patches, updating revocation lists, and employing advanced monitoring tools, organizations can mitigate the risks posed by CVE-2024-7344. Strengthening firmware security is essential to maintaining the overall resilience of modern computing environments.
Secure your systems today to safeguard against the evolving threat landscape.
Related posts:
- How to Download offline setup of Microsoft Store App
- Mitigate WinVerifyTrust Signature Validation Vulnerability CVE-2013-3900
- Microsoft Streaming Service Elevation of Privilege Vulnerability (CVE-2023-29360)
- Microsoft MSHTML Remote Code Execution Vulnerability
- [Solved] How to solve Windows update error 0x800f0831- CBS E_STORE_CORRUPTION
- How to Use GenAI Prompting for Security Vulnerabilities
- BeyondTrust Privileged Remote Access and Remote Support products Vulnerability (CVE-2024-12356 & CVE-2024-12686
- Chained for Attack: OpenVPN Vulnerabilities Leading to RCE and LPE
- March 2025 Patch Tuesday: A Stabilizing Security Landscape
- CVE-2025-24991: Unmasking the Windows NTFS Out-Of-Bounds Read Vulnerability
